Introduction to the Internet of Things (IoT), Node Red, and the Raspberry Pi
Cybersecurity First Principles in this lesson
-
Abstraction: An abstraction is a representation of an object or concept. It could be something such as a door, a speedometer, or a data structure in computer science. Abstraction decouples the design from the implementation. The gauges in an automobile are an abstraction of the performance of a car. A map is an abstraction of the earth.
-
Least Privilege: One of the ways to protect information is by limiting what people can see and do with your information and resources. The principle of least privilege says to allow the minimum number of privileges necessary to accomplish the task.
-
Minimization: Minimization refers to having the least functionality necessary in a program or device. The goal of minimization is to simplify and decrease the number of ways that software can be exploited. This can include turning off ports that are not needed, reducing the amount of code running on a machine, and/or turning off unneeded features in an application. This lesson focuses specifically on turning off ports that aren’t in use.
-
Modularization: The concept of modularity is like building blocks. Each block (or module) can be put in or taken out from a bigger project. Each module has its own separate function that is interchangeable with other modules.
-
Resource Encapsulation: Encapsulation is an object oriented concept where all data and functions required to use the resource are packaged into a single self-contained component. The goal is to only allow access or manipulation of the resource in the way the designer intended. An example, assume a flag pole is the object. There are fixed methods on how the flag pole is to be used. Put the flag on, take the flag off, raise or lower the flag. Nothing else can be done to the flag pole.
-
Simplicity: Simplicity allows a person to better understand hardware and software. Without the clutter of unnecessarily complicated code and interfaces, the software will be more understandable by people that will update the code when requirements change. It will be easier to understand by the testers and they will be able to spot problems sooner. By keeping the software as simple and as focused as possible, the reliability and security are greatly increased.
Introduction
Lets build an IoT device – wait, just what is the IoT – and why should I care? I’m afraid to ask – is it secure?

In this lesson, we will take a close look at IoT and the associated security implications by building a simple IoT application on a Raspberry Pi using a program called Node-Red.
Goals
We will continue our work towards our GenCyber camp purpose with the below goals for this lesson:
- Use Node-Red to develop a simple IoT application on a Raspberry Pi
- Integrate the If This Then That (IFTTT) service as an IoT cloud service
- Recall how the Cybersecurity First Principles of abstraction, least privilege, minimization, modularization, resource encapsulation, and simplicity apply to IoT applications
Materials Required
- Raspberry Pi
- Internet connection
Prerequisite lessons
### Table of Contents - Cybersecurity First Principles in this lesson - Introduction - Goals - Materials Required - Prerequisite lessons - What is the IoT - A Simple IoT Example - Step 1: Install and update needed programs - Step 2: Start Node-Red - Step 3: Start Firefox - Step 4: Create an IFTTT account - Step 5: Create your first Node-Red flow - Step 6: Link flow to IFTTT - Step 7: Build an IFTTT Recipe - Step 8: Test it! - A Second Example - Step 1: Add a new flow - Step 2: Build your new flow - Step 3: Test it! - Evaluation - Additional Resources - Acknowledgements - License
What is the IoT
The IoT is the term applied to the many internet connected devices now occupying space in our lives. Take a look through your house. You may have phones, tablets, laptops, fitbits, televisions, thermostats, smoke detectors, bathroom scales, refrigerators, light bulbs, and who knows what else all connected to the internet.
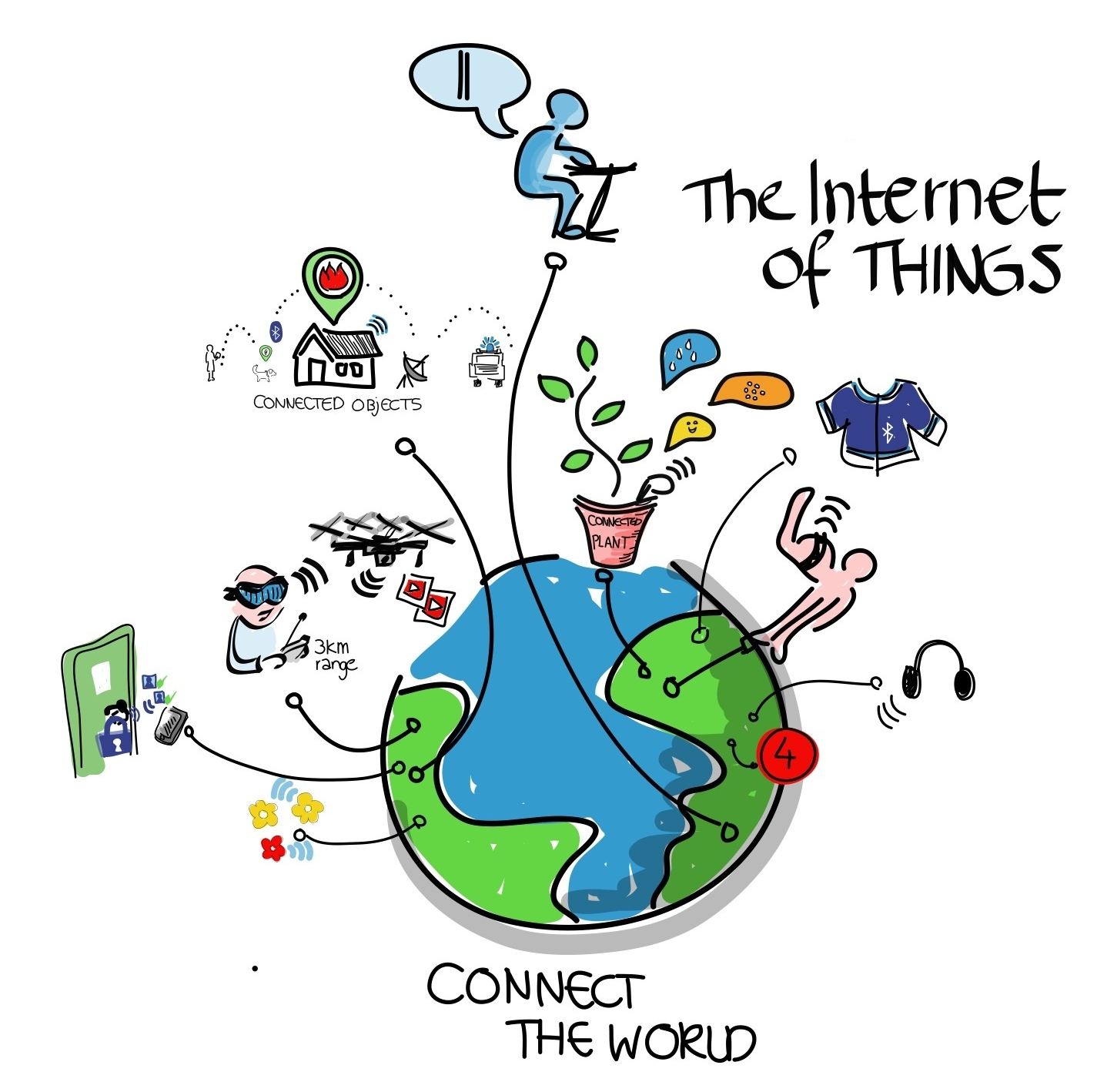
These devices communicate with you, perhaps a cloud server, maybe even each other. Although some devices such as phones or tablets have very powerful operating systems and security features, many IoT devices such as thermostats or fitbits don’t have security features due to the added cost and drain on batteries. Is that a problem? The general consensus amongst security experts is this is like running with scissors. It may help you get a task done but at some point, you may find the results painful. Where do we start with addressing the issue? Let’s start by taking a very generalized look at an IoT device.
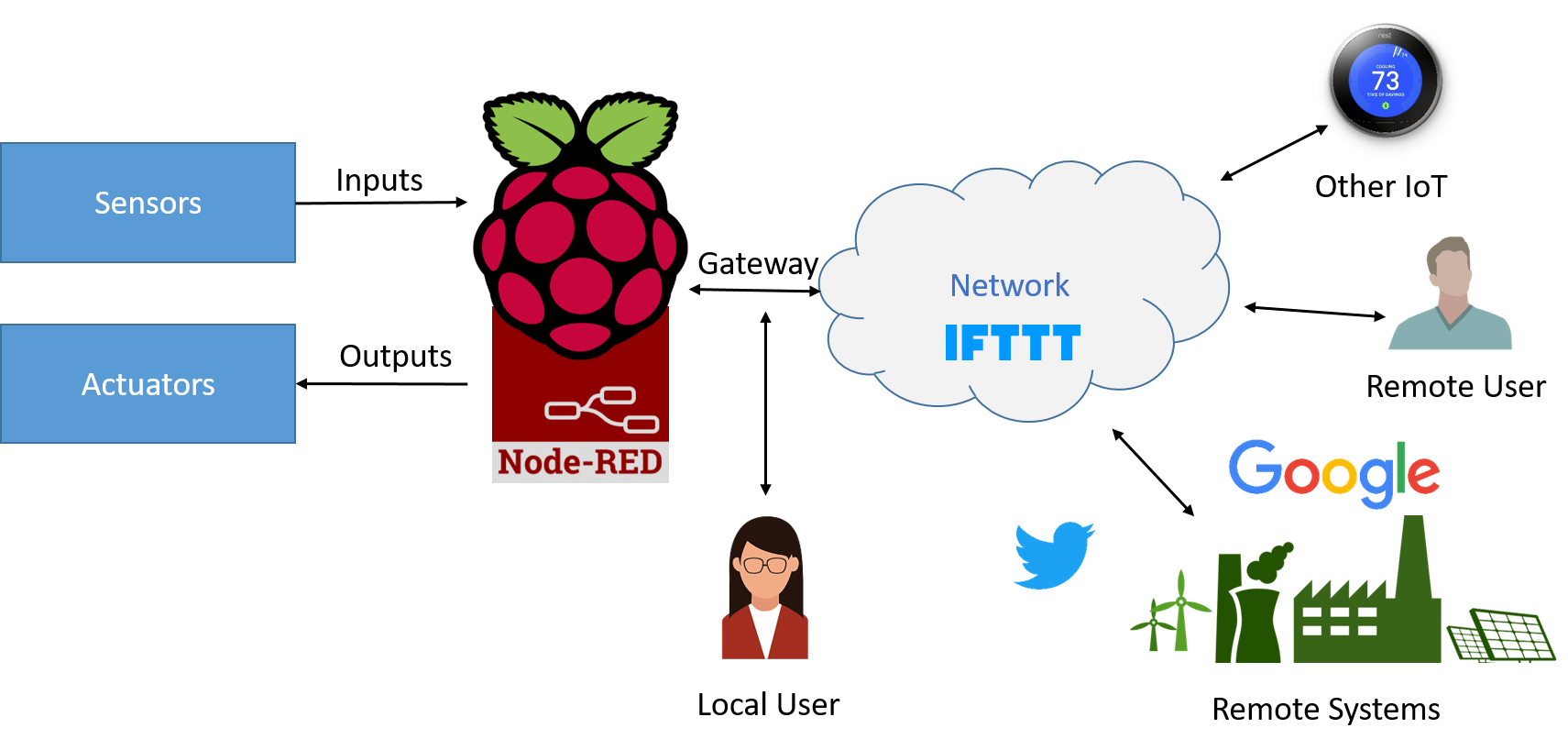
In a very general sense an IoT device is a device that may have sensors (inputs) such as thermometers or light detectors, actuators (outputs) such as switches or alarms, a processor (like your Raspberry Pi running Node-Red) to make sense of the data and direct actions, and a gateway (network connection) to interact with users and other systems. An IoT device can make our lives much easier, or if someone who wants to do harm gets access to the device they could steal data or take control of objects in your house or business.
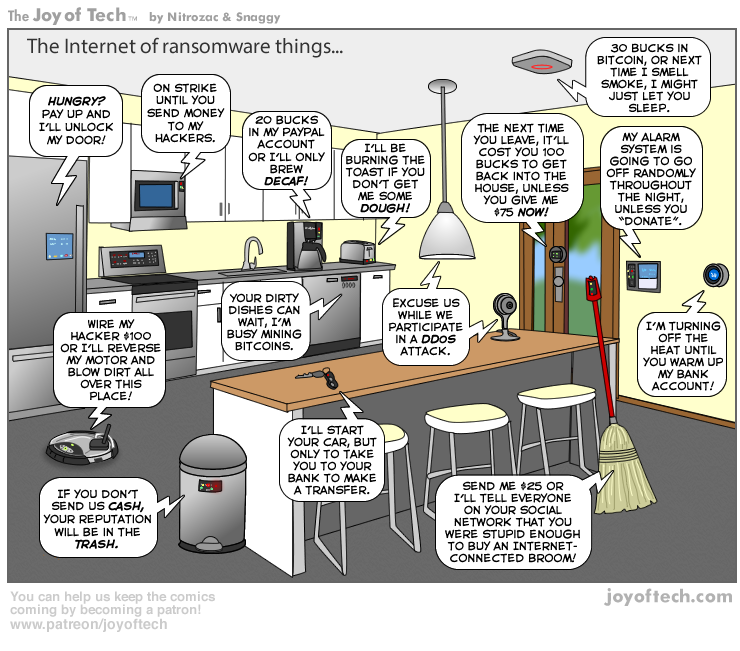
- Discuss with students some of the ways compromise of IoT devices could lead to harm, perhaps through information leakage or loss of control of devices.
By properly applying the Cybersecurity First Principles we can reduce the risk that someone can take over our IoT device and cause us harm. The platform we will use to explore the IoT is our Raspberry Pi running a program called Node-Red. Lets jump right into it.
A Simple IoT Example
Step 1: Install and update needed programs
The first thing we need to do is install and update a few needed programs. As much as we would like to have all the programs we would ever need loaded on a system not only does allowable memory not allow this it’s not a good idea from a cybersecuirty perspective. The First Principle of minimization tells us that by reducing the amount of places where vulnerabilities could exist we make our system more secure. We call this reducing our attack surface. Having programs loaded you are not using makes you needlessly open to attacks to those programs.
During the below installs respond yes to any prompts you receive during the following operations.
- Install the Firefox Browser - Node-Red works best with Firefox. Remember we need to use the command
sudoto preface the install command due to the Raspberry Pi implementing the Cybersecurity First Principle of Least Privilege.
sudo apt-get install firefox-esr
- Install npm - This will allow us to install additional capabilities, called nodes, into Node-Red
sudo apt-get install npm
sudo npm i -g npm@2.x
- Update Node-Red - this operation may take several minutes
update-nodejs-and-nodered
- Install nodes for the IFTTT service and Raspberry Pi camera. Note: If you receive an error that the .node-red directory does not exist go under the rasperry menu (first on the left), select programming, and node-red. This will create the directory. Then enter the command
node-red-stopfrom a terminal window. This will shutdown the program so you can continue with installs. After that you can continue with the below instructions
cd ~/.node-red
npm install node-red-contrib-ifttt
npm install node-red-contrib-camerapi
Step 2: Start Node-Red
On the Raspberry Pi desktop select Menu, Programming, Node-RED
Step 3: Start Firefox
On the Raspberry Pi desktop select Menu, Internet, Firefox ESR
Step 4: Create an IFTTT account
IFTTT (If This Then That) is a cloud service that allows us to automate actions, if the service receives a certain input, then it will execute a pre-selected action. We will use the IFTTT service with Node-Red to interface with some common cloud services.
- In Firefox, navigate to https://ifttt.com and click Sign up
- Walk through the online instructions to create your account
- Once registration is complete, click search and enter Webhooks

- Click the Connect button
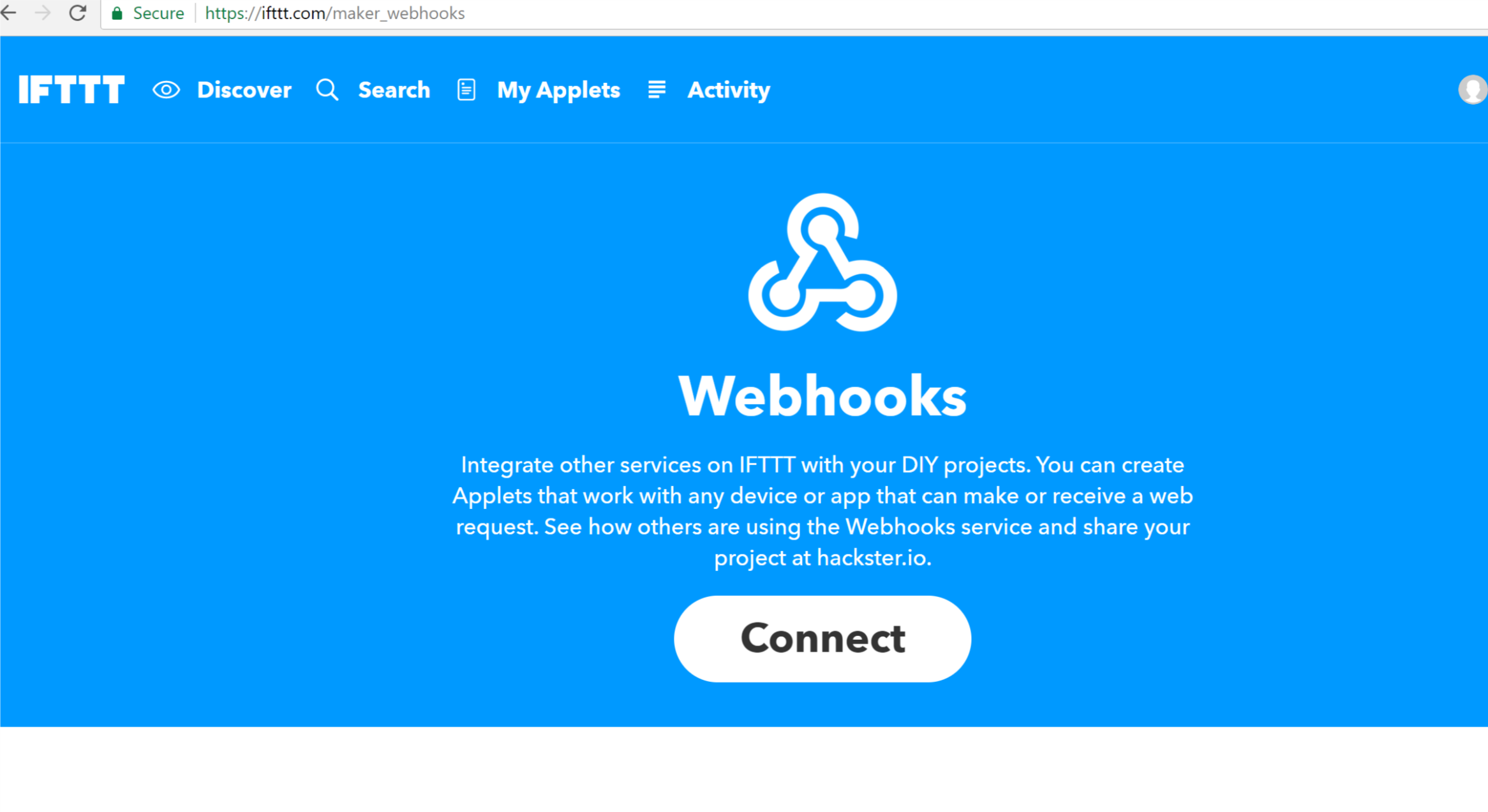
- We are done with the IFTTT web site for now but don’t close the tab yet, we’ll be back here shortly
Step 5: Create your first Node-Red flow
Programs in Node-Red are called flows and they can be very simple or very complex. We will keep our first flows very simple but you will see you can do quite a bit with a simple flow. Flows are made up of connected nodes. Although each node is a single element in a flow there may be several actions which that flow generates. This implementation of nodes and flows illustrate several examples of Cybersecurity First Principles:
- Simplicity: A flow simplifies all the activity which is being conducted in the background. By studying a flow you can quickly get an idea of what actions are being executed. This aids security as you can quickly understand the overall actions taking place vice getting lost in all the details.
- Abstraction: Each node presents a single action, however, there may be several steps occurring in the background. The details are abstracted behind the node which represents the interior actions.
- Modularization: Each node is a building block in a flow. Nodes can be swapped out to change the functionality of a flow without requiring changing the entire flow.
- Resource Encapsulation: You are unable to directly access several of the interior functions which are necessary for a flow to work. Due to this internalization, or encapsulation, critical functions are protected from external misuse.
With those principles in mind, lets start your first flow.
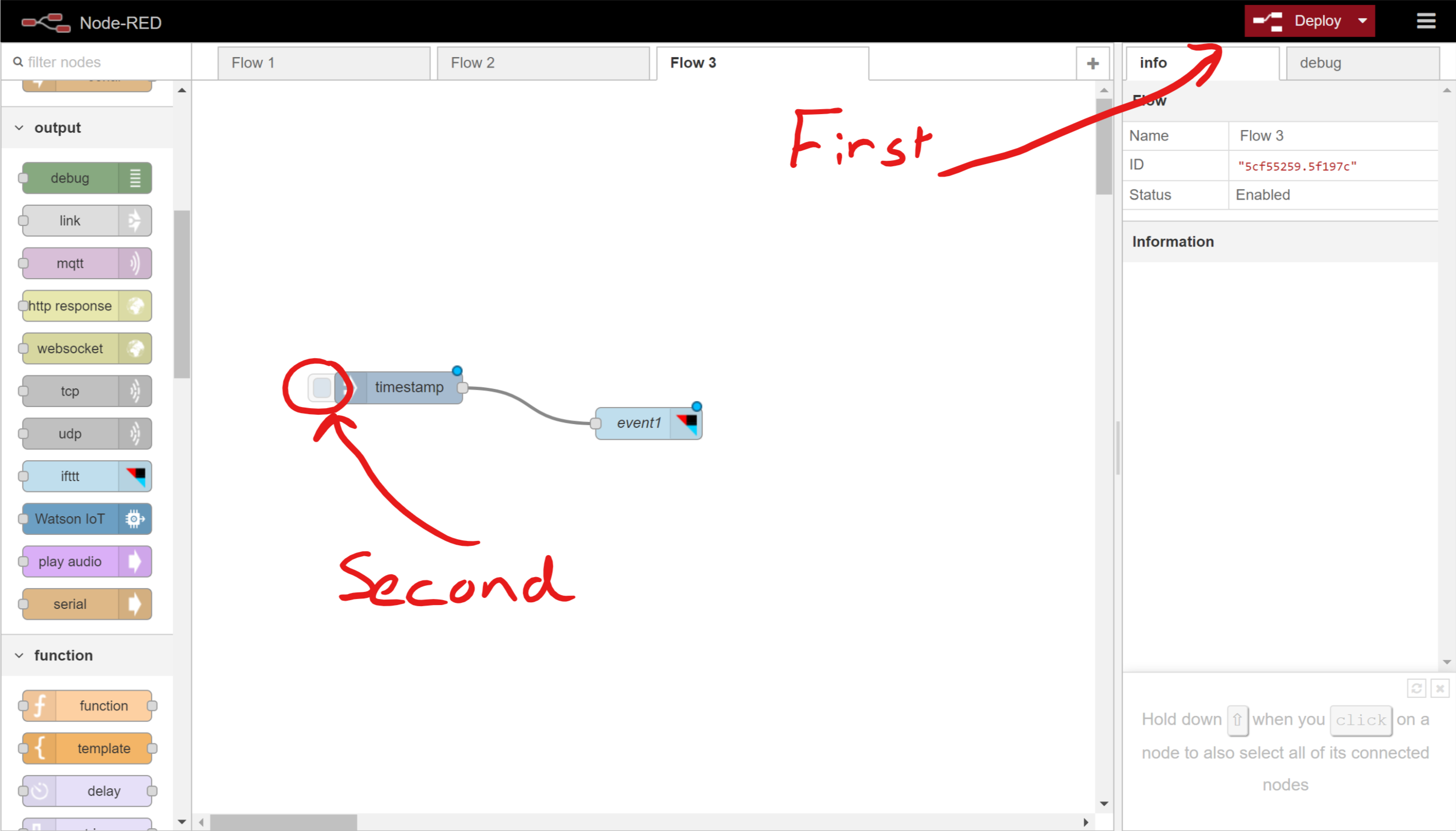
- Open a new tab in Firefox (keep the IFTTT tab open for now) and enter the address http://127.0.0.1:1880, this will bring up the web page for the Node-Red server running on your Raspberry Pi.
127.0.0.1is always the local address of the computer you are using. - Drag a inject node from the left pane, called the palette, into the flow, once you drag it into the field it’s title will change to timestamp
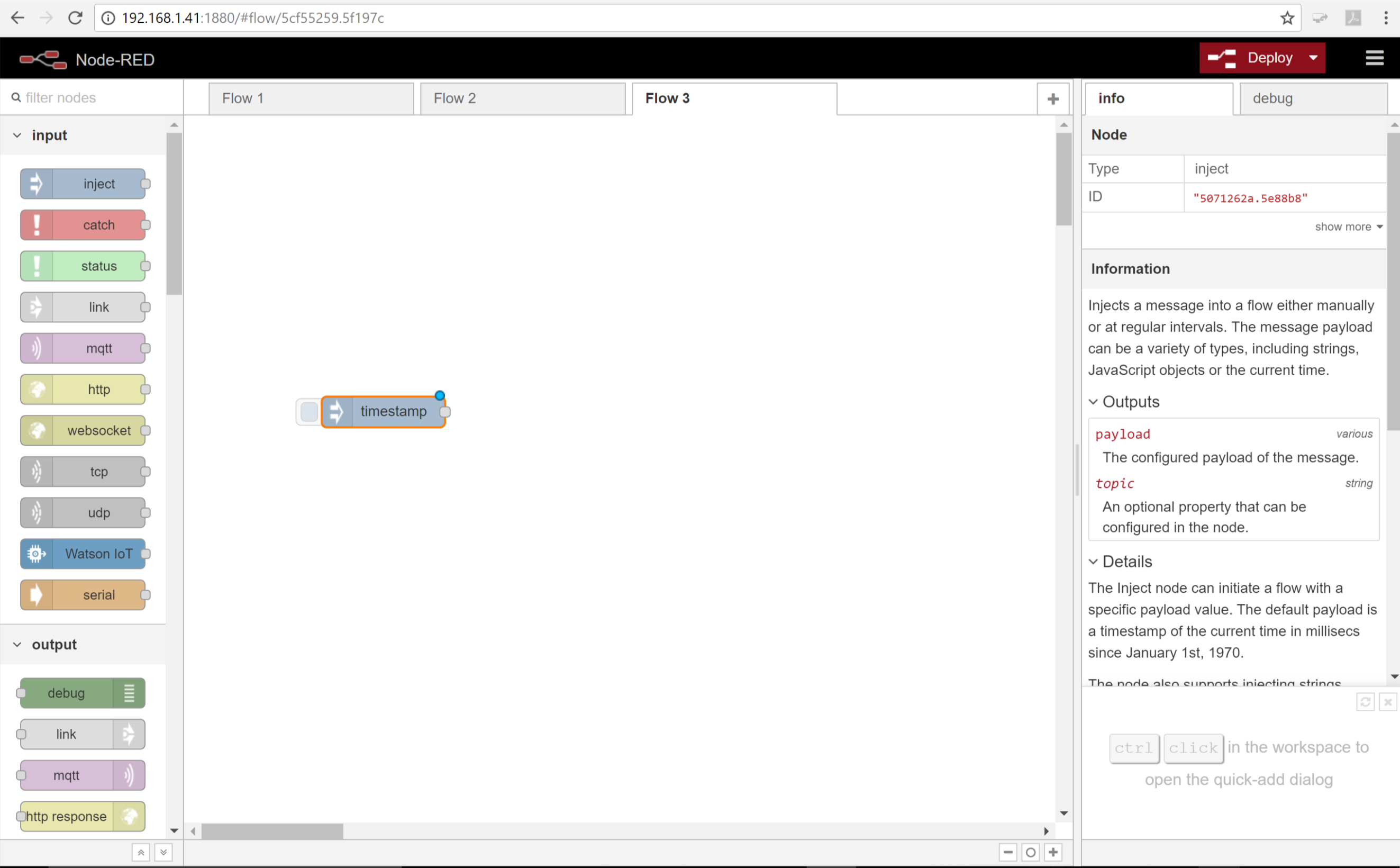
You will notice on the right-hand side of the screen a description of the node is given. This particular node returns the current system time when you click the button on the left side of the node. For this flow we don’t care about the time on the timestamp, we will just use it to indicate the button was pressed.
- Now scroll down through the palette and locate the IFTTT node under the output section and drag it into the flow.
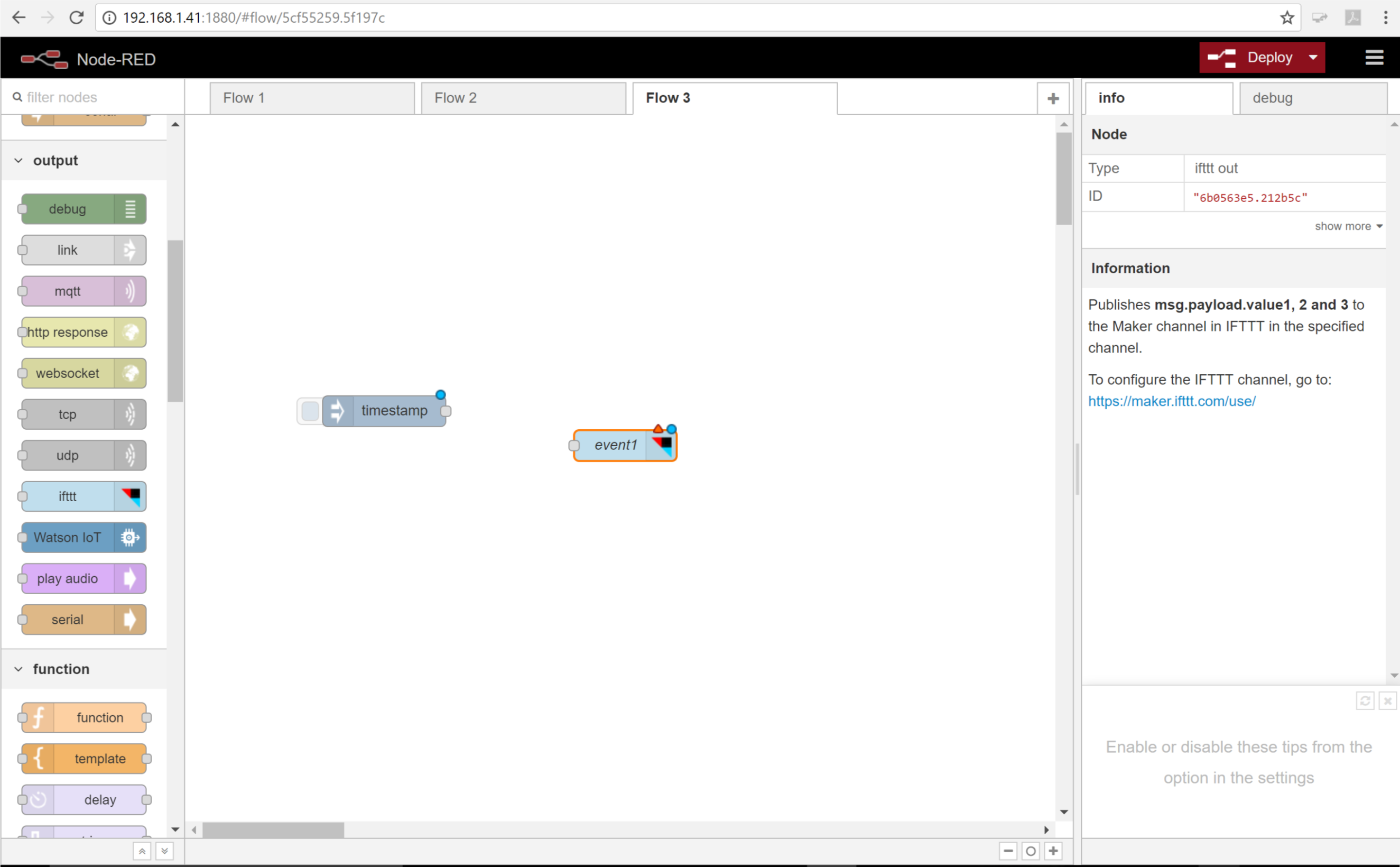
- Now we need to connect the two nodes. Click the dot on the right side of the inject node and drag a connection line to the dot on the left side of the IFTTT node.
Your flow is now built but we still need to link it to your account on IFTTT.
Step 6: Link flow to IFTTT
Remember the Cybersecurity First Principles of Abstraction and Resource Encapsulation? Now we get to take a closer look at how those principles are implemented.
- Double click on the IFTTT node, you will see a dialog box displayed which allows us to give the node some of the information it needs to do its job. Notice, you are not setting variables directly but entering them through a dialog. This is Resource Encapsulation and allows error checking and security checks to be done behind the scenes.
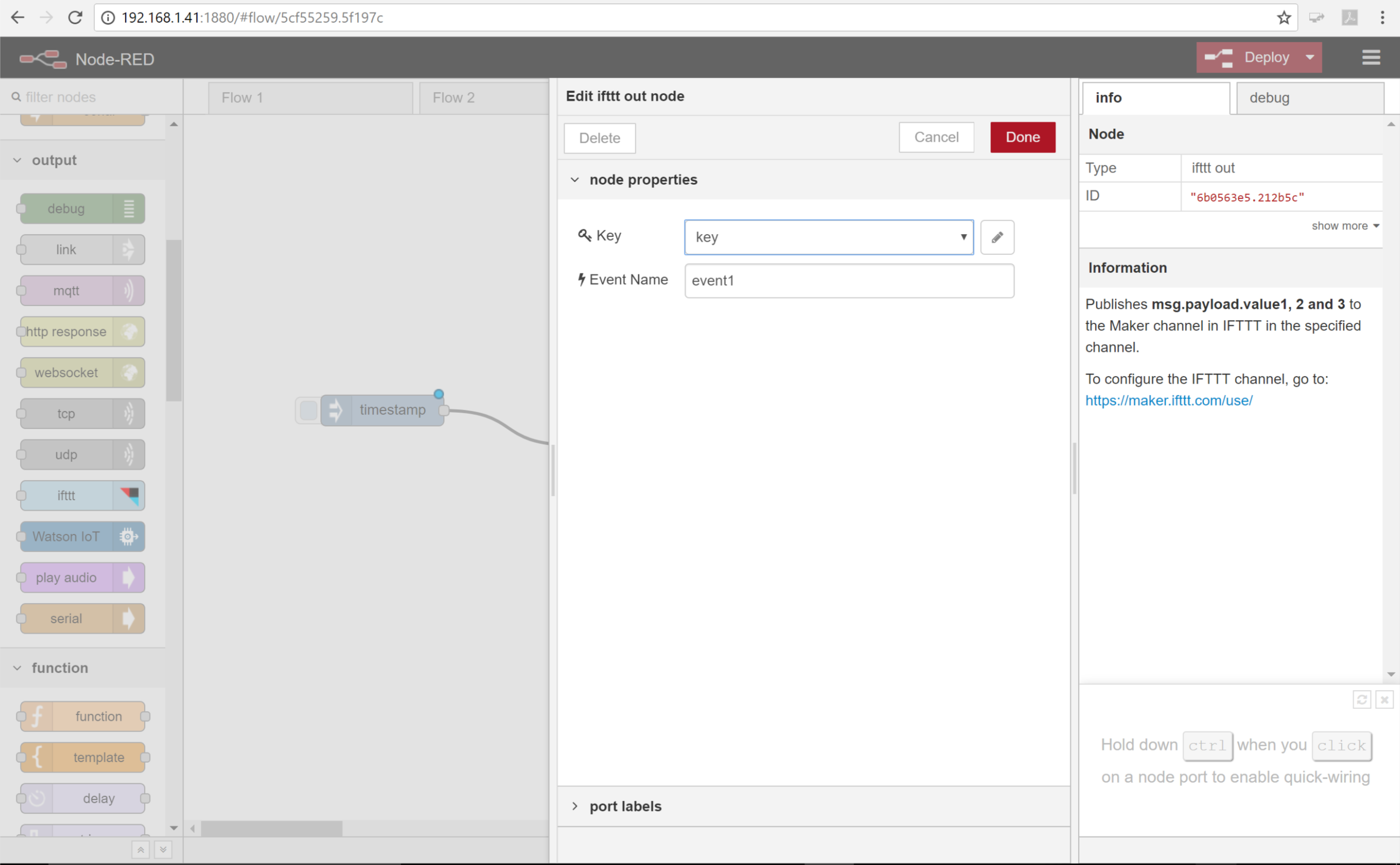
Now we need to fill in the first field named key. This is a unique identifier which links this flow to your IFTTT account. To get this value you will need to go back to the browser tab for IFTTT.com
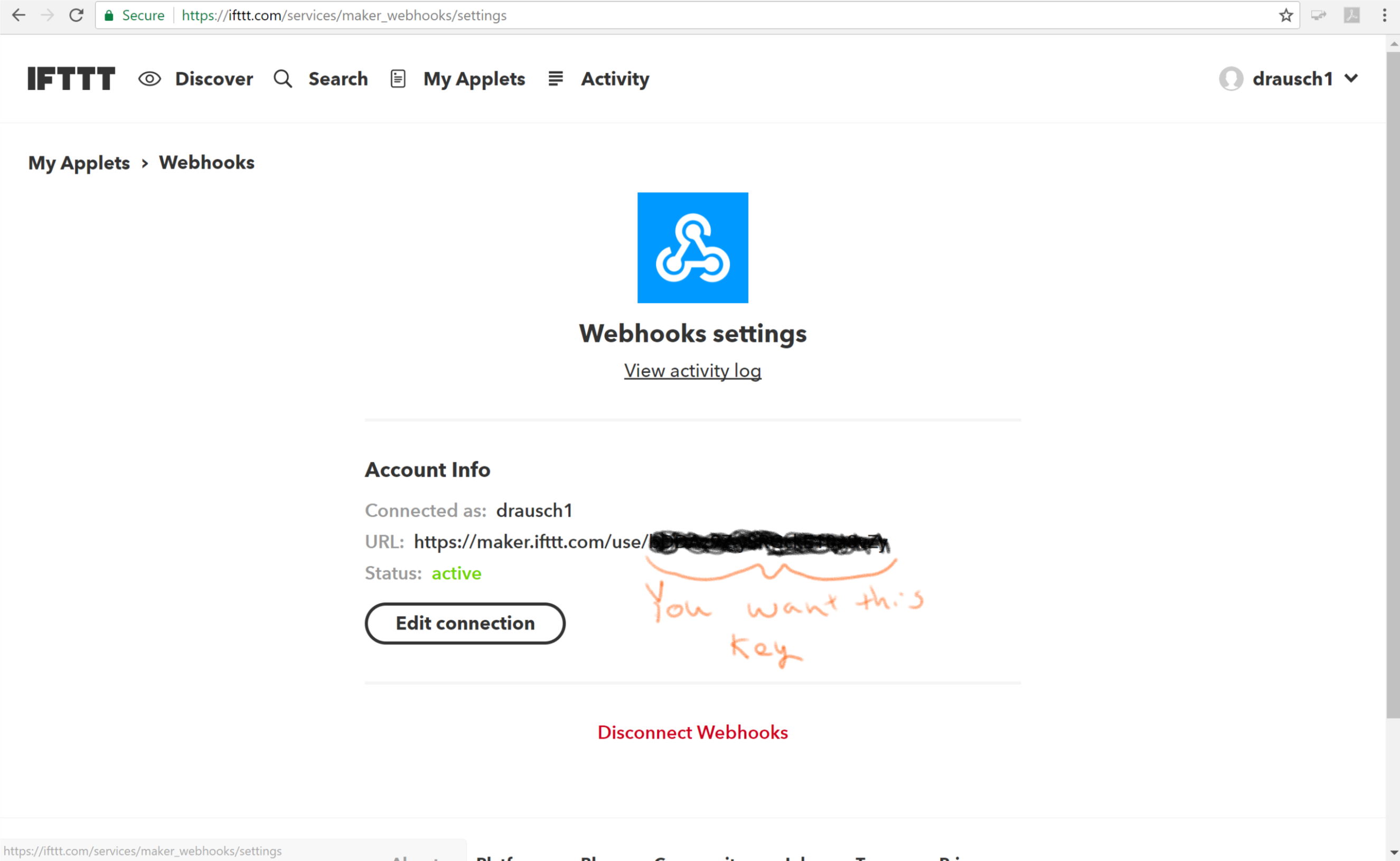
- Once you are back at IFTTT click the settings button. The identifier you want is the last part of the URL which is blocked out on the image below. Everyone’s key is different, you need to use your key to link to your IFTTT account. Select and copy this key.
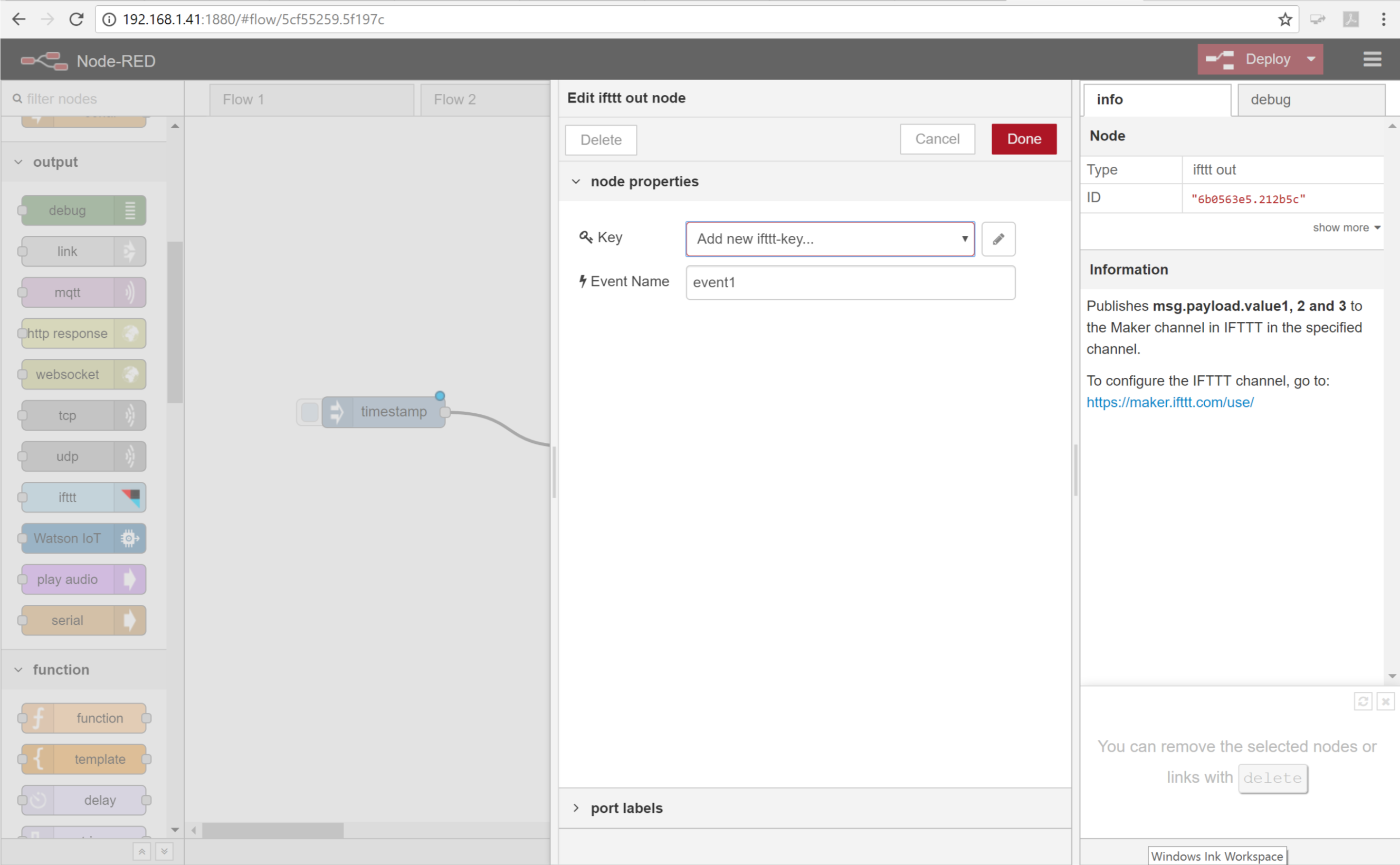
- Go back to the Node-Red tab in your browser and click the key field. Click Add new ifttt-key… and then click the pencil next to the field.
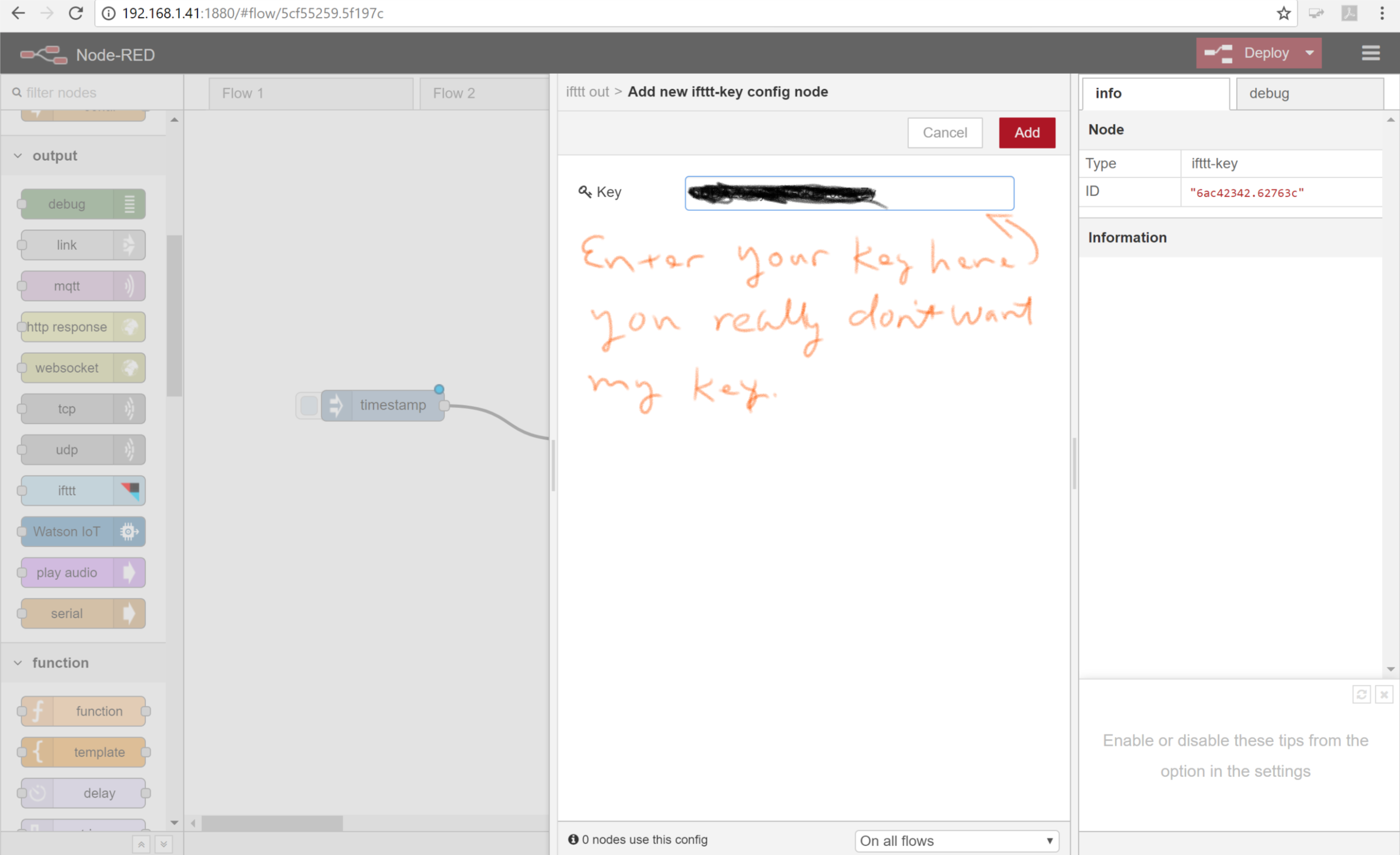
- Paste the key you just copied from IFTTT into the field. Click Add.
-
Leave the Event Name field with the default
event1. You can change this to something more descriptive but remember what it is because we will need it later. -
Click Done.
Step 7: Build an IFTTT Recipe
Your flow is now built and configured but we need to tell the IFTTT service what to do if it gets activated. We do this through building an IFTTT recipe.
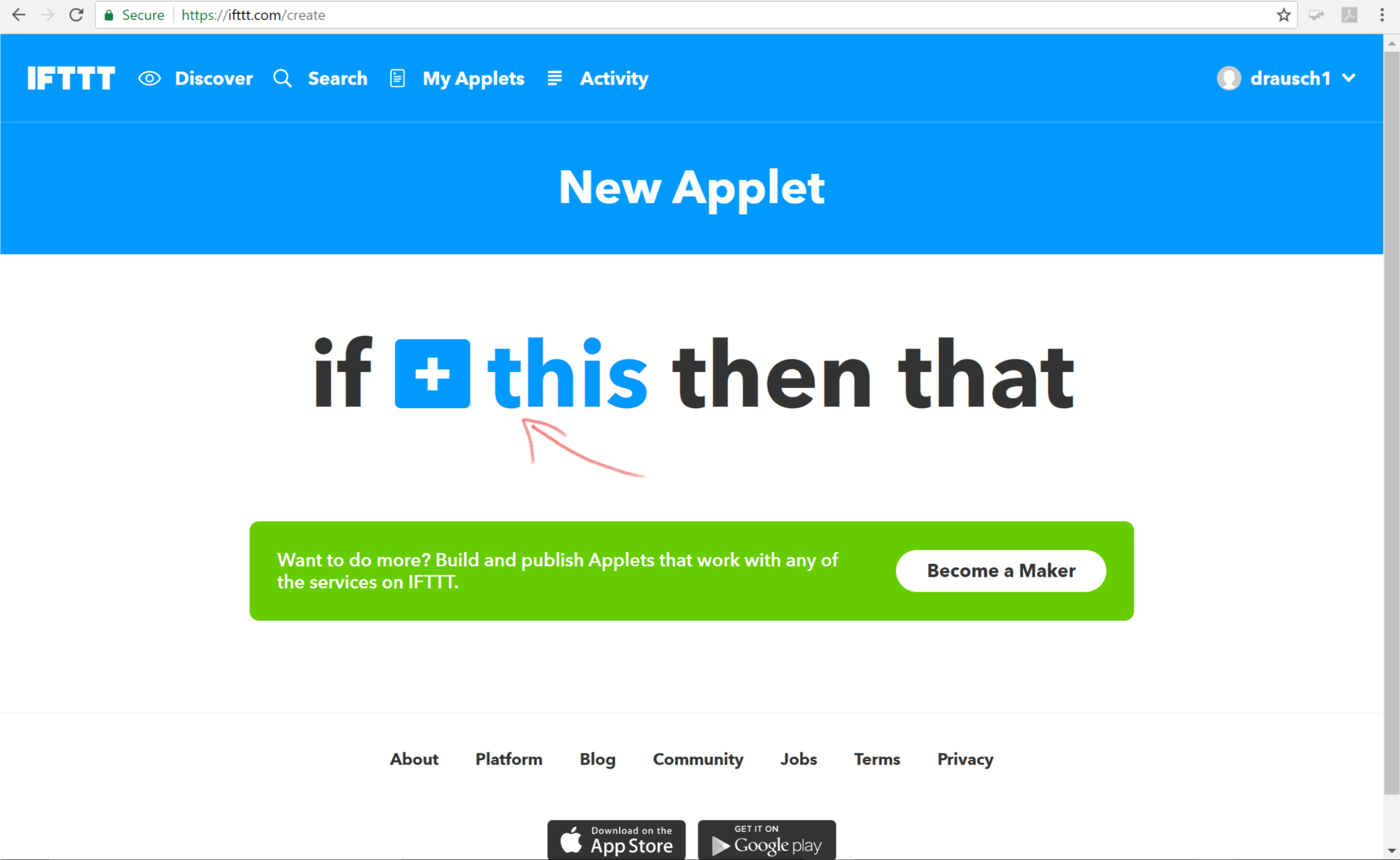
- Go back to your IFTTT browser tab. If it got closed, use the address https://ifttt.com/my_applets
- Click on New Applet
- Click on the + this to set the trigger
- In the Choose a Service search field enter Webhooks and select the Webhooks service displayed

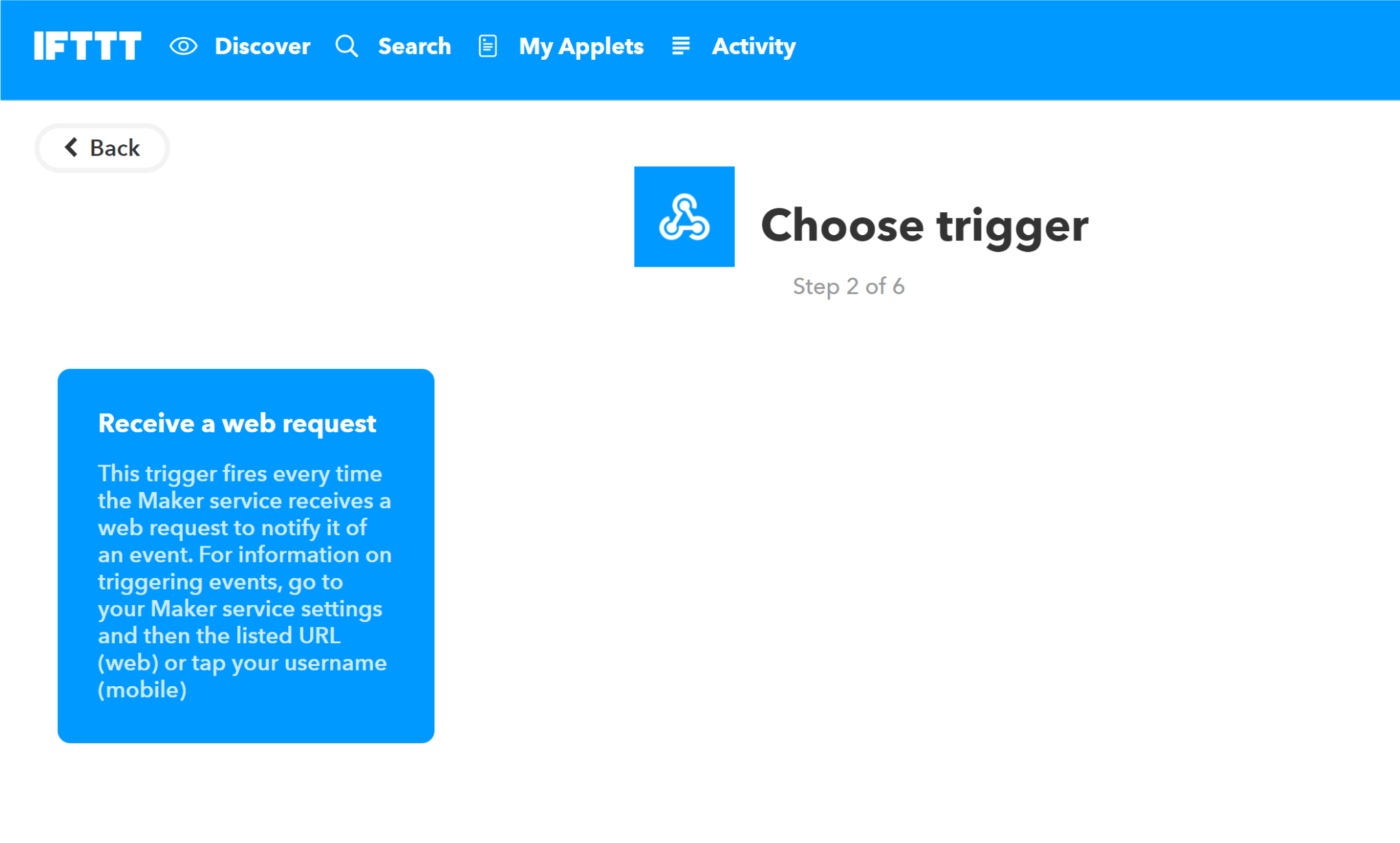
- On the choose a trigger screen select Receive a web request
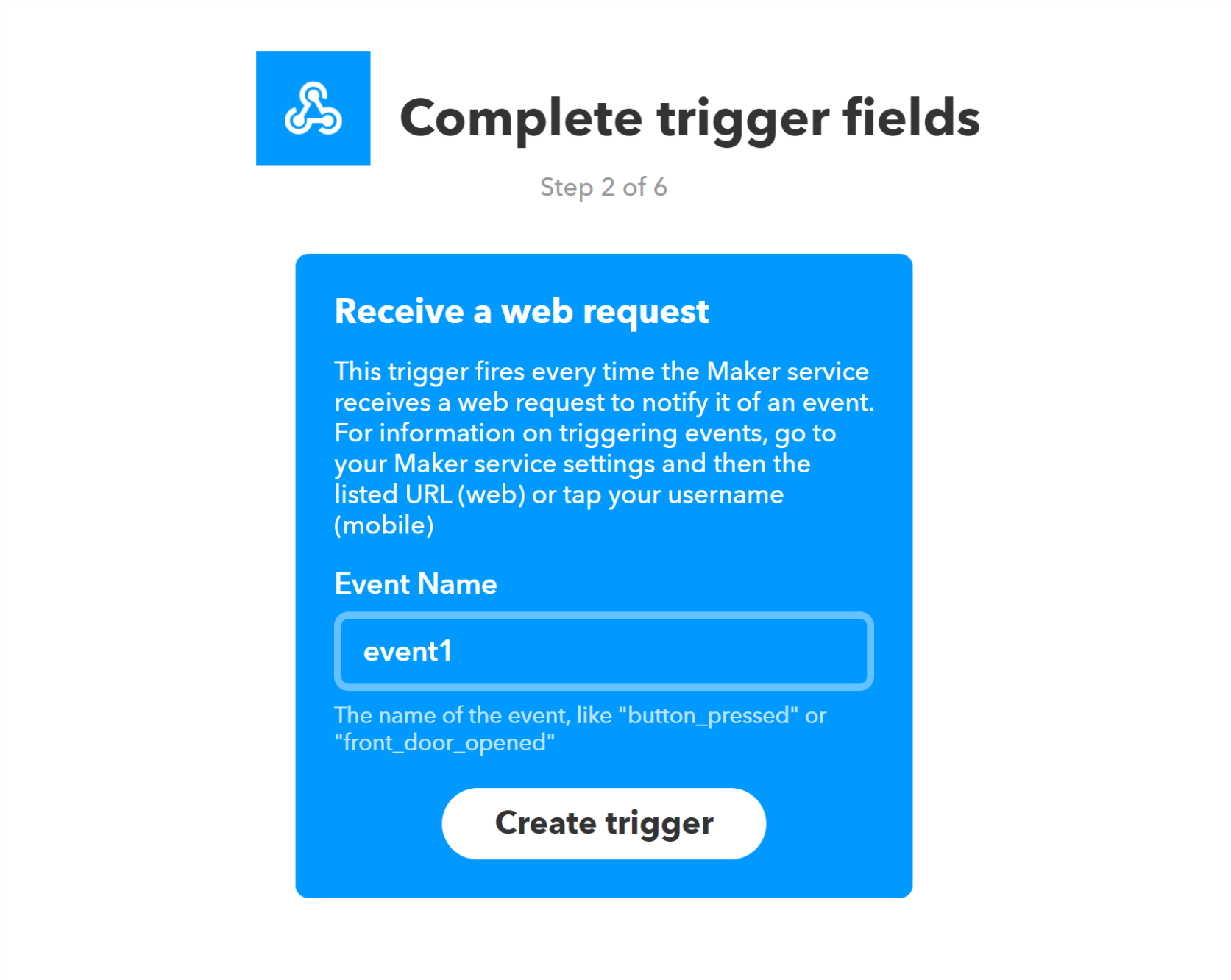
- In the Event Name field enter
event1. If you named your event something else in Node-Red you should enter that here
-
Click Create Trigger
-
You now get to tell IFTTT what it should do when it receives the trigger. Take a moment to look through all the options. We are going to send an email. Click the email service tile.
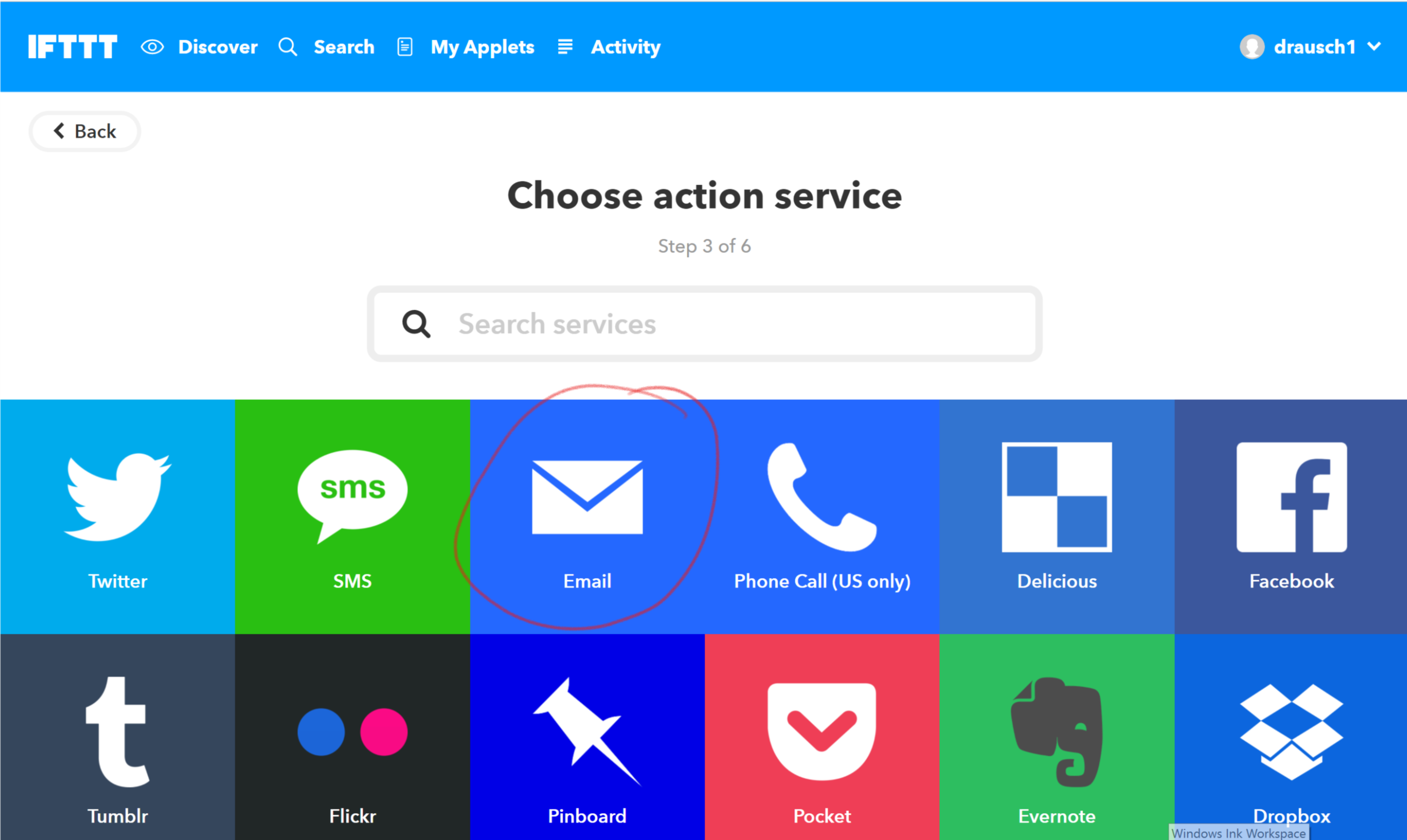
- You now have the opportunity to customize what the email will say when it is sent. You can pass data between Node-red and IFTTT. For now, we will use the default values. This will send an email to the address you used to register when you created your IFTTT account. Click Create Action.
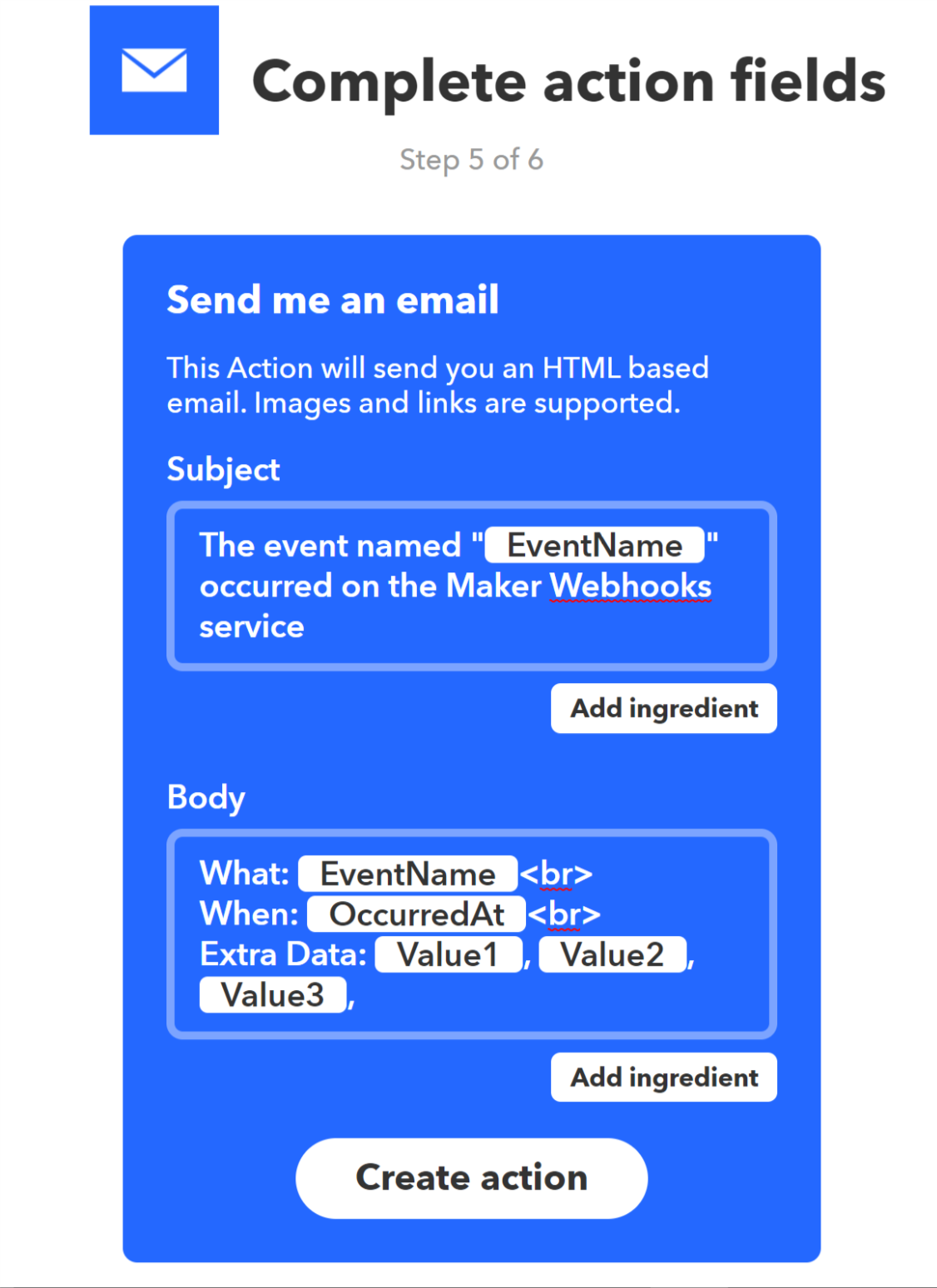
- Congratulations! You have built your first recipe. Click Finish
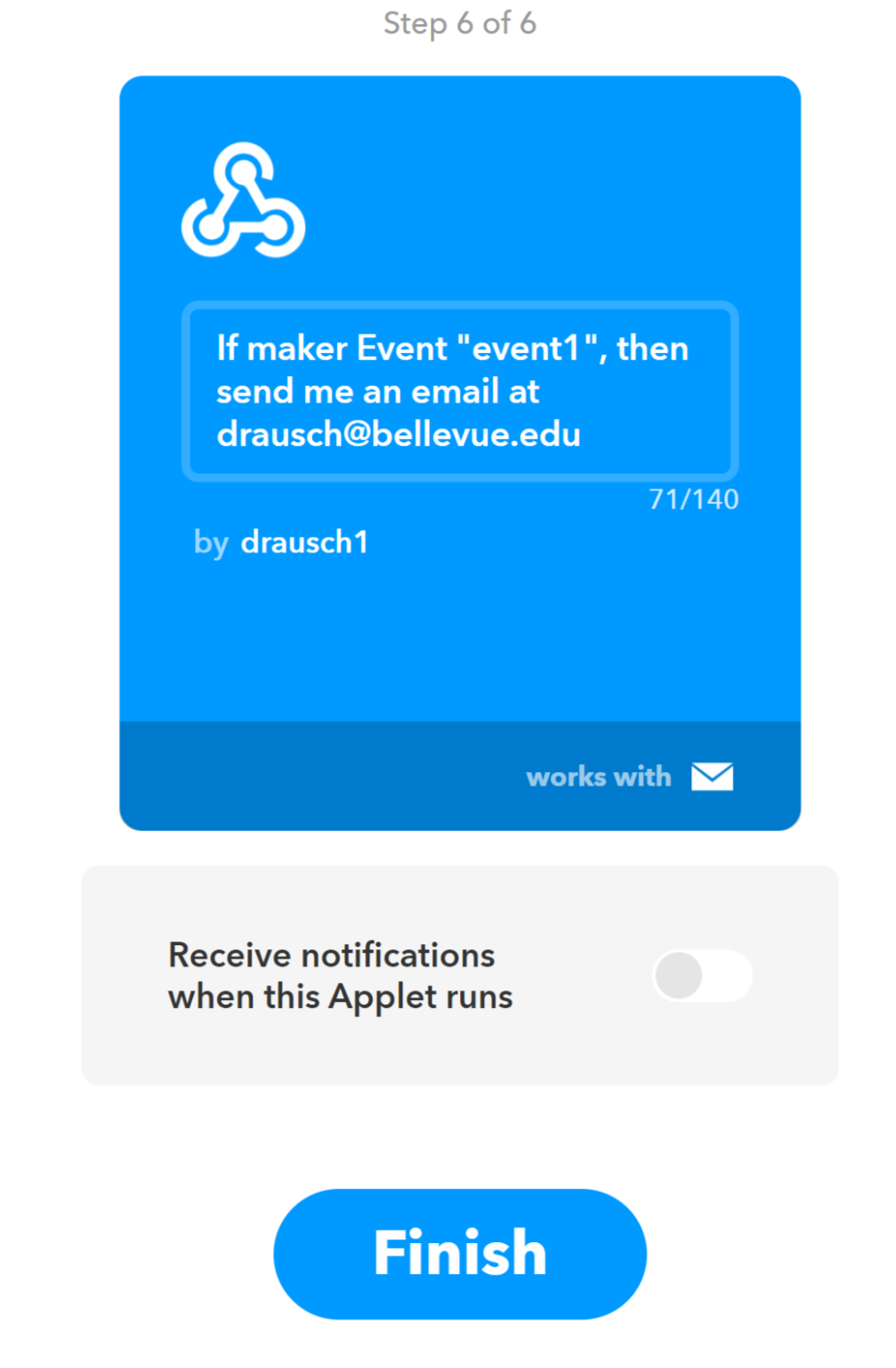
Step 8: Test it!
We have now built our flow and the supporting recipe. To test the flow we must first deploy it and then activate the timestamp node.
- Click the Deploy button at the top right of the screen
- Click the button on the left side of the timestamp node
If you did everything correctly you will receive an email telling you that the timestamp button was pressed. Although this was very simple and perhaps not very useful think about what how this could be expanded. Maybe instead of clicking the timestamp node, the IFTTT is triggered by an external switch that activates whenever your pet goes out their pet door. Now your pet will send you an email when it goes out into the yard!
A Second Example
Let’s try a second example that doesn’t use the IFTTT service. In this example we will build a new flow that swaps out the IFTTT node for a camera node - remember that principle of Modularization? Here it is in action.
Step 1: Add a new flow
We will begin by adding a new flow, that way the one you created will still be active.
- Click the plus to the right of the flow names, this will open a new tab for your new flow.
Step 2: Build your new flow
You’ve already built one flow, this one will follow the same procedures. Add an inject node, a camerapi node (under the Raspberry Pi section of the pallet), and connect them. Your completed flow should look like the below.
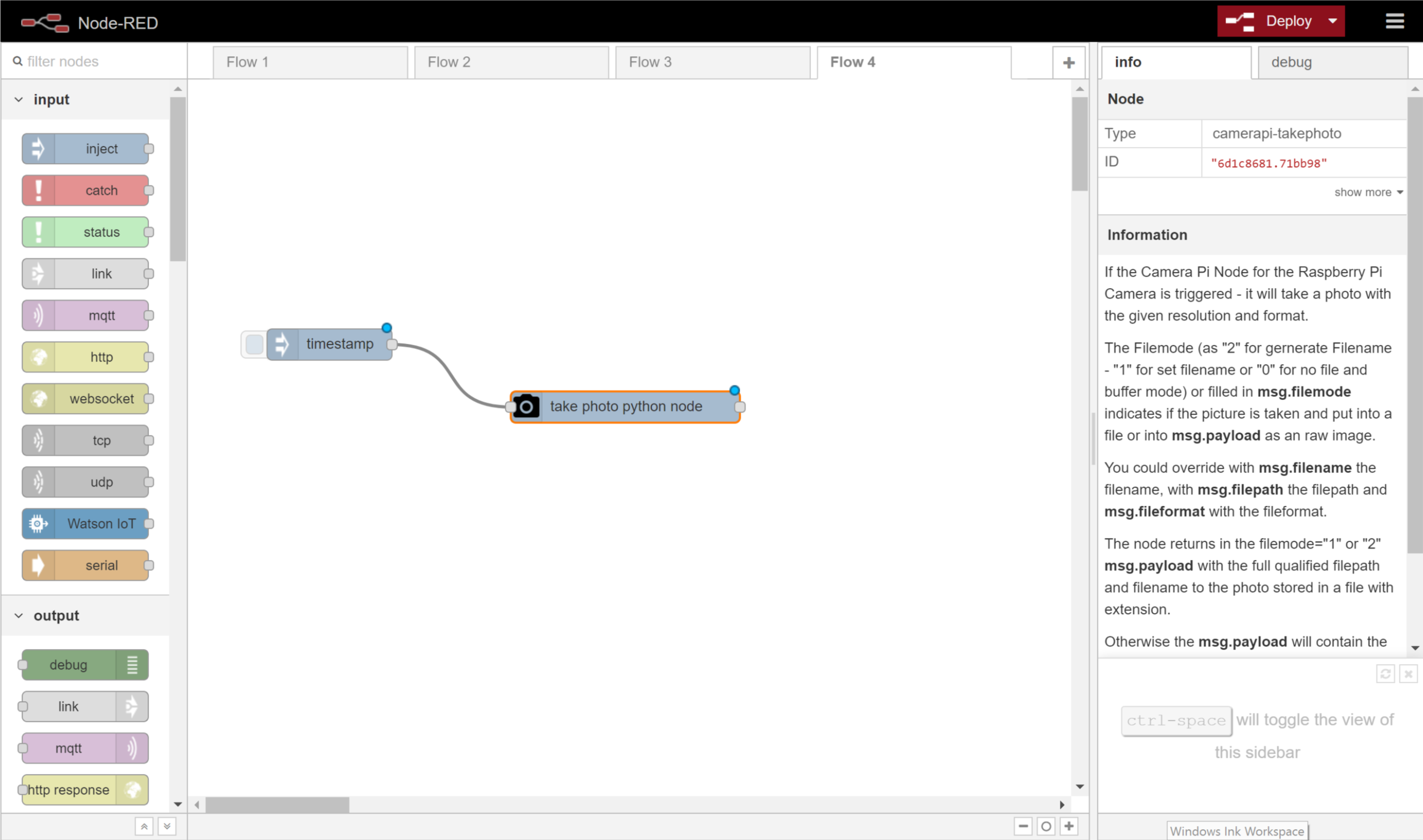
Step 3: Test it!
We are going to use the default settings for the nodes for this flow. The camera node, when activated, will take a photo with the Pi’s camera, give the photo a unique (and very long) filename, and store it in the /home/pi/pictures directory. You can configure the node to give custom file names and set picture formats, sizes, and orientations.
- Deploy your new flow
- Click the timestamp inject button
- You can view the picture you just took by going to the Pi desktop, clicking Menu, Accessories, File Manager. Click the Pictures folder and double click your photo to view.
Discuss with the class how these features could be used in an IoT device. Maybe the inject is triggered with a sound, takes a photo, and emails it to you - your own burglar alarm!
Spend some time exploring the Node-Red nodes. What else could you build?
Evaluation
Use Kahoot to assess comprehension
- Which Cybersecurity First Principle addresses how nodes can be replaced with other nodes in a flow to modify features? Modularization.
- Which Cybersecurity First Principle addresses how you are unable to directly access the inner workings of a node but must set parameters through dialogs? Resource Encapsulation.
- Each node represents a single action, however, there may be several steps hidden in the background is an example of? Abstraction.
- An IFTTT program is called a what? Recipe.
- When you use the IFTTT node in a flow which element or action represents the use of least privilege? webhooks key.
Additional Resources
For more information, investigate the following:
Acknowledgements
License
Nebraska GenCyber 
is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
Overall content: Copyright (C) 2017-2018 Dr. Matthew L. Hale, Dr. Robin Gandhi, Dr. Briana B. Morrison, and Doug Rausch.
Lesson content: Copyright (C) Doug Rausch 2017-2018.

This lesson is licensed by the author under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.